Containerization and virtualization are two terms you may often hear in the tech world. These concepts have completely transformed IT infrastructure and software distribution, making businesses more efficient, scalable, and adaptable. This blog post will go into great detail about containerization and virtualization, looking at what they are, how they work, and the main differences between them.
What are Virtualization and Containerization?
Containerization and virtualization emerge as leading approaches used by technology development companies for application hosting in computer systems, each offering distinct advantages. These mechanisms play critical roles in modern IT infrastructures, catering to diverse needs and contributing to efficient resource management.
What Is Virtualization Technology?
Virtualization is the process of generating a virtual version of a physical resource, such as a server, storage device, or network. It enables various operating systems and applications to run independently on the same physical hardware.
The market for virtualization technologies is experiencing rapid growth, driven by the increasing demand for data-driven insights across industries. The global virtualization technologies market is projected to exceed $11 billion by 2030.
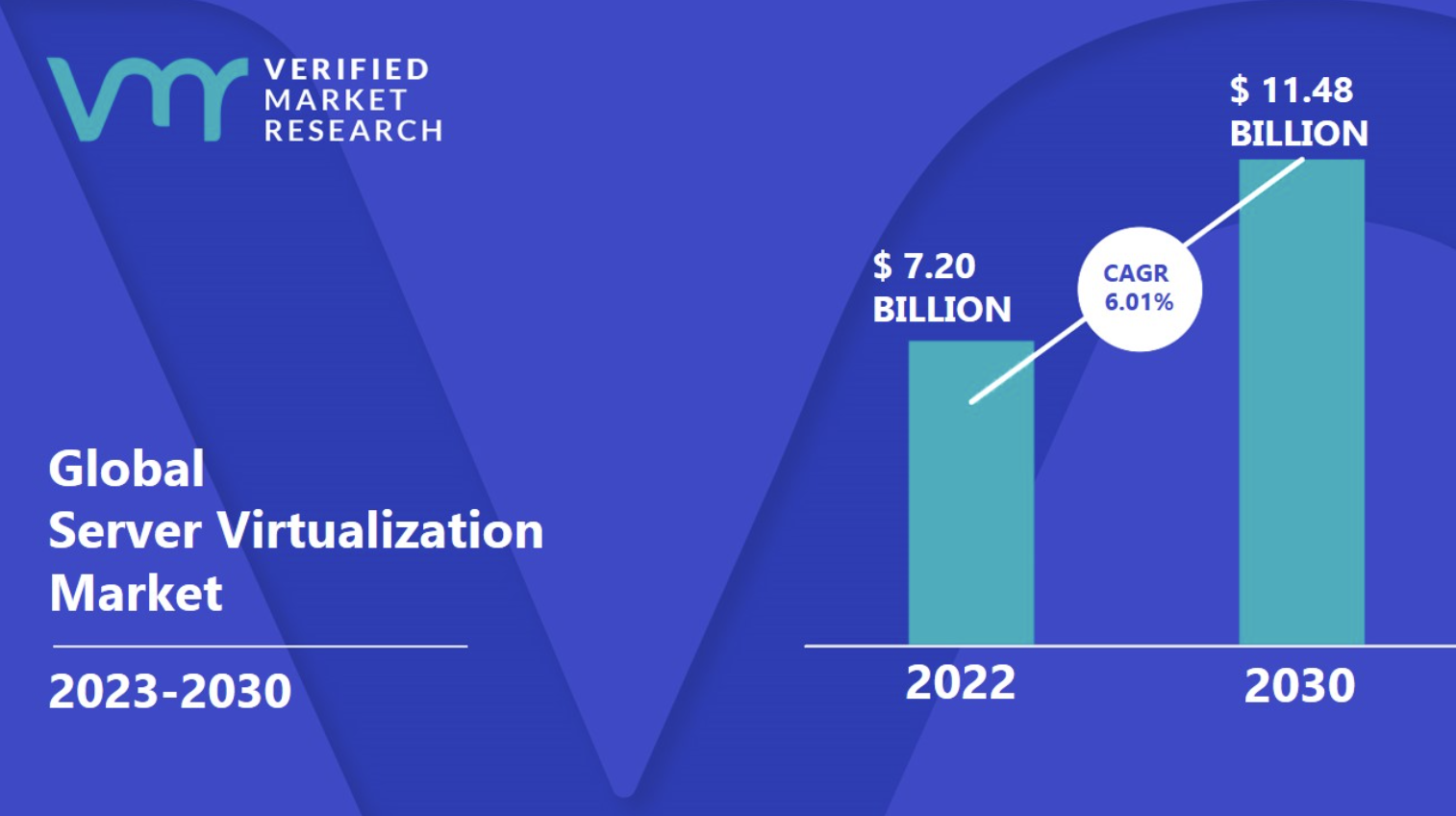
Types of Virtualization
Virtualization technology has been around for a long time and has evolved into multiple types, each with a distinct function.
Server Virtualization
Server virtualization enables the creation of multiple virtual servers on a single physical server, thereby maximizing resource utilization and reducing hardware costs. It isolates applications and their operating systems from the underlying hardware, allowing multiple instances to run simultaneously.
Desktop Virtualization
Desktop virtualization allows users to access a virtual desktop environment hosted on a centralized server, enabling flexibility and remote access. This approach is especially beneficial when employees need to work remotely or from different devices.
Network Virtualization
Network virtualization abstracts physical network components such as switches and routers and creates virtual networks that can be managed independently. It offers flexibility in network configuration, resulting in simpler management and more efficient use of resources.
Storage Virtualization
Storage virtualization abstracts physical storage devices, enabling the creation of virtual storage pools that can be easily allocated and managed. It provides a unified view of storage resources and allows for efficient scaling and provisioning.
What Is Containerization?
Containerization is a relatively new paradigm that focuses on lightweight virtualization of applications. However, according to the forecasts, the global application container market has enormous potential and could reach over $30 billion by 2030.
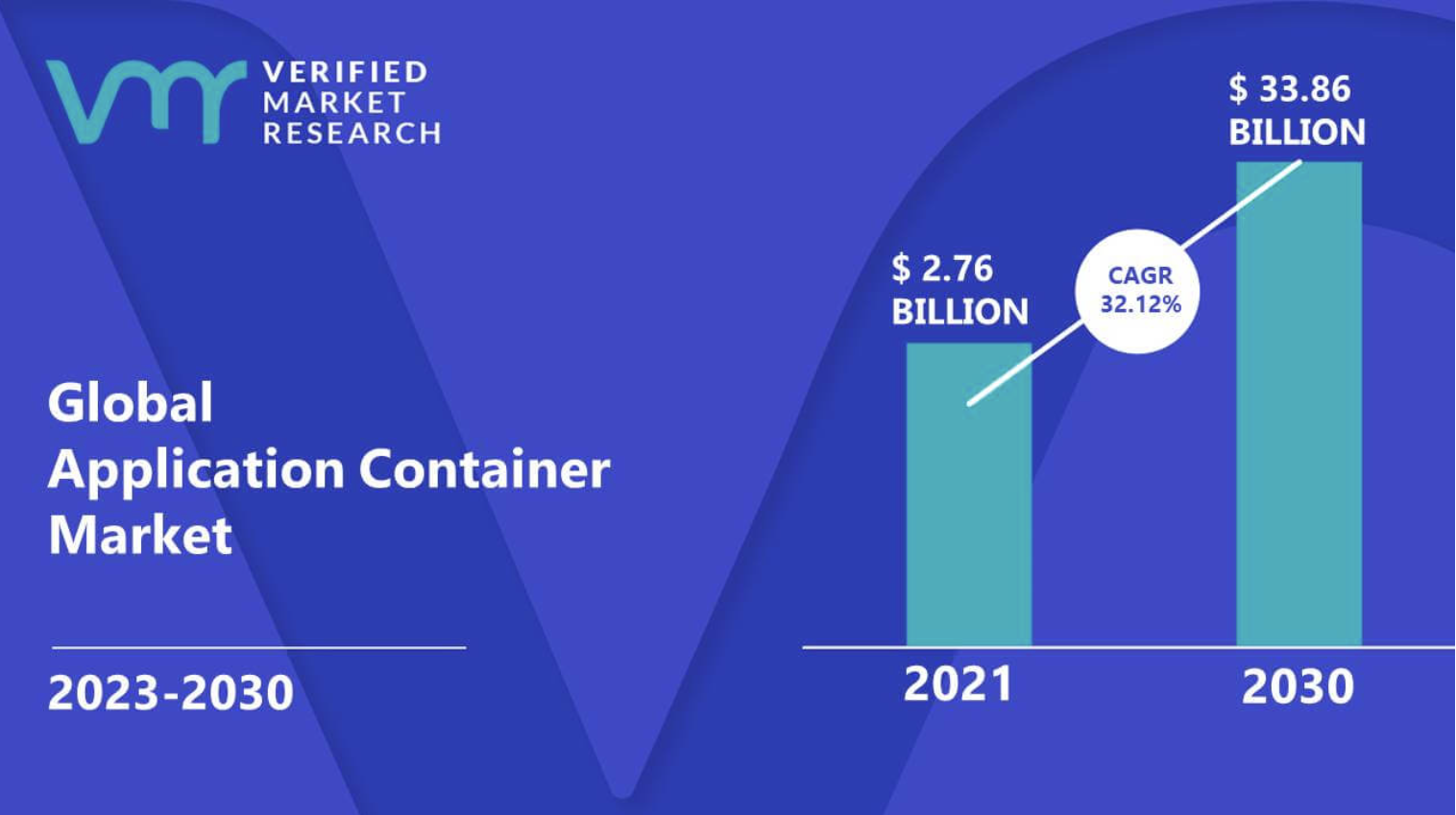
Containerization allows applications to be packaged with their dependencies in a portable container. Containers provide isolation and encapsulation, enabling applications to run consistently across different computing environments.
Containerization Types
Containerization encompasses various types, and some prominent containerization types include the following.
- Docker containers: Docker is a widely adopted containerization platform that encapsulates applications and their dependencies into lightweight, portable containers. These containers can run consistently across different environments, promoting scalability and efficiency.
- Pods in Kubernetes: Kubernetes, an open-source container orchestration system, introduces the concept of pods. A pod is the smallest deployable unit in Kubernetes and can encapsulate one or more containers. Containers within the same pod share the same network namespace and storage, facilitating seamless communication.
- Linux containers (LXC): LXC is an operating system-level virtualization method for running multiple isolated Linux systems on a single host. It provides a lightweight alternative to traditional virtualization, allowing for efficient resource utilization.
- rkt (Rocket): Developed by CoreOS, rkt is a container runtime designed with security and simplicity in mind. It aims to provide a composable, secure, and standards-based containerization solution.
- Windows containers: Similar to Docker containers but tailored for Windows environments, Windows Containers allow developers to create and deploy applications within isolated, portable containers on Windows Server.
These containerization types cater to diverse needs, enabling developers and IT professionals to choose the solution that best fits their requirements for application packaging, deployment, and scalability.

Containerization vs. Virtualization: Difference Between Virtualization and Containerization
While both containerization and virtualization offer benefits for IT infrastructure management, there are fundamental differences between the two approaches:
- Resource utilization. Virtualization technologies allow for consolidating multiple virtual machines on a single physical server, providing better resource utilization. In contrast, containerization shares the host operating system and kernel, resulting in even higher resource efficiency. Containers require fewer system resources compared to virtual machines.
- Isolation. Virtualization provides complete isolation between virtual machines, with each VM having its operating system instance. In containerization, containers share the same operating system kernel, resulting in a lighter and more efficient means of isolation. However, this shared kernel also means an issue in one container can potentially impact others on the same host.
- Startup time. Containers have faster startup times compared to virtual machines as they do not require booting an entire operating system. Containers can start within seconds, making them ideal for microservices architectures and rapidly scaling applications. Virtual machines have longer startup times due to the need to boot an entire operating system for each instance.
- Portability. Containers are highly portable across different computing environments, making migrating applications between various cloud providers and on-premises infrastructure easier. Virtual machines, although portable, require additional configuration and setup steps when moving to different environments. Containers provide a consistent deployment model, reducing deployment complexity and time.
Benefits of Virtualization
Virtualization technologies offer a range of advantages, providing organizations with enhanced operational efficiency and flexibility by leveraging innovative approaches to resource management. These benefits contribute to streamlined processes and improved overall IT infrastructure.
Cost Savings
Virtualization allows for better utilization of hardware, reducing the number of physical servers required and lowering energy costs. Consolidating multiple virtual machines onto a single physical server significantly improves resource usage.
Flexibility and Scalability
Virtualized environments are highly flexible and scalable, enabling organizations to quickly adapt to changing business demands. Virtual machines can be provisioned and de-provisioned dynamically, enabling efficient resource allocation.
Disaster Recovery and Backup
Virtualization simplifies disaster recovery and backups by encapsulating entire virtual machines, making it easier to restore them in case of a hardware failure or data loss. Virtual machine snapshots and replication provide efficient backup and restore capabilities.
Containerization Benefits
Containerization presents a suite of advantages, fostering operational efficiency and flexibility through modernized resource utilization strategies. These benefits contribute to streamlined processes and enhanced IT infrastructure, aligning with contemporary software deployment and management trends.
Efficiency
Containers are lightweight and require fewer system resources, enabling organizations to run more applications on a single host. They provide fast startup times, reducing latency and improving overall application performance.
Simplified Deployment
Containers provide consistent deployment across different environments, eliminating compatibility issues and reducing deployment time. Developers can work on developing containerized applications in their preferred environment and have confidence that the containers will work reliably in production.
DevOps and Continuous Deployment
Containerization technology is a key enabler of DevOps practices, allowing for faster testing and iterative deployments. Containers make it easier to manage application dependencies and ensure consistent runtime environments across different stages of the software development lifecycle.
Scalability
Containers can be easily scaled horizontally, with multiple containers running the same application in parallel, delivering high availability and improved performance. Container orchestration platforms like Kubernetes simplify the management of containerized applications at scale.

Security Considerations in Containerization and Virtualization
While containerization and virtualization technologies offer many benefits for IT infrastructure management, security is an area that requires careful consideration. Because both approaches involve multiple instances running on a single physical host, they can increase the attack surface and introduce security risks beyond those of traditional physical systems.
Containerization Security
- Isolation: Containerization tools provide a level of isolation from the host operating system, but they are not completely isolated from each other. Containers in the same host may share the same kernel, which means that if an attacker gains access to a container, they may be able to access other containers on the same host. This is why ensuring that each container has only the minimum required privileges to fulfill its functionalities is essential.
- Sensitive data leakage: When designing containerized applications, it’s crucial to consider how sensitive data should be stored. As containers are portable, there is a risk that sensitive data may leak into the container image or be accidentally exposed during deployment and runtime. Thus, encryption techniques should be applied to sensitive information, both at rest and in transit.
- Vulnerability management: Containers frequently update with patches and new software versions, which means that timely updating of container images is essential to maintain a secure deployment. It is vital to have a policy in place to minimize the time it takes to assess, test, and deploy critical patches and updates for container images.
- Access control: Access control mechanisms should be implemented to ensure that only authorized personnel can access and modify container environments. This includes mechanisms to authenticate, authorize, and audit users and activities.
Virtualization Security
- Hypervisor security: Virtual machines rely on hypervisors to manage the physical resources underneath them. Hypervisor vulnerabilities can expose virtual machines to attack. Thus, it is essential to keep hypervisors updated with the latest patches and ensure they are properly configured based on best security practices.
- Resource control: With virtual machines, providing a separate instance of the operating system and the application environment is essential. This offers better resource isolation and reduces the risk of one virtual machine impacting others on the same host. However, virtual machines may need to share the host’s CPU, memory, storage, and network resources, so resource allocation and control are essential.
- Network security: Virtual machines and containers rely on shared hardware and software resources to communicate with each other and the outside world. It is essential to isolate network segments and implement access controls and firewall rules to limit the impact of network-based attacks.
- Lifecycle management: Managing the lifecycle of virtual machines involves setting up, configuring, monitoring, and decommissioning them. Security must be an essential component of this lifecycle, where access controls, monitoring, and auditing activities must be in place to mitigate the risks.
Overall, security considerations are an essential part of both containerization and virtualization. As organizations adopt these technologies, they must have a robust security strategy in place by choosing a reliable technology development company to ensure they are mitigating the risks inherent in these approaches.
Conclusion
In summary, containerization and virtualization are powerful technologies that have changed IT infrastructure and application deployment. Both approaches have their advantages and use cases, and organizations should carefully consider their specific needs and requirements when determining the best strategy for their IT infrastructure.
By understanding the differences and benefits of containerization and virtualization, organizations can make informed decisions about the deployment models that align with their business goals, ensuring improved efficiency, agility, and scalability in their IT environments. Whether it’s virtualizing servers, desktops, networks, or storage or adopting containerization tools for microservices architectures, embracing these technologies will undoubtedly contribute to the success and scalability of modern IT infrastructure.




